The numbers are wild. According to the Melapress WordPress Security Survey, 96% of site owners faced a security incident this year. That’s almost everyone.
Expect it to get worse.
Today’s hackers aren’t only running simple brute-force scripts that blindly try every possible combination of characters until they find the right one for the login credentials.
They’re using AI-infused tools that learn. Tools that adapt to your site’s defenses. Tools that play offense in real time, just like the AI you use for content or design.
So, here’s the question we all should be asking ourselves:
If cybercriminals keep getting smarter, shouldn’t your WordPress website security do the same?
But many businesses? Still don’t know how to secure a WordPress site in this new landscape.
Yes, the usual WordPress vulnerabilities get exploited daily. That’s not exactly breaking news.
But the sophistication behind those attacks in 2025? That’s something else—AI-powered exploit kits, plugin supply-chain breaches, automated credential harvesting.
The natural extension of these advancements is — we need more than a “set and rest” security approach. Layered, proactive, and tech-driven measures to stand strong.
If you’re looking for another “install this plugin and you’re safe” guide, this isn’t it.
This one’s written from the front lines of WordPress operations — by people who work with WordPress every day. Who test its limits and evolve their WordPress security best practices as fast as the threats evolve.
Let this be your heads-up from Mavlers to tighten your defenses before the next wave of attacks tests your setup.
WordPress website security in 2025: What new threats are lurking
Let’s start with hard facts.
As per Patchstack, 7,966 new security vulnerabilities were discovered in the WordPress ecosystem in 2024.
This year, that number is climbing, and over 41% of those vulnerabilities are actually exploitable in real-world conditions.
Said another way: With growing surface, attackers now have smarter tools to find and weaponize weaknesses.
1. Old weaknesses, new tactics
The familiar WordPress website security holes haven’t gone away:
- Weak logins
- Outdated WordPress security plugins
- Poor file permissions
- Insecure hosting setups
These are still the easiest portals to get into.
The difference is that, in 2025, cyberattackers are weaponizing automation and AI to exploit them faster and in a more targeted fashion.
A single outdated plugin might serve as a launchpad for multi-layered attacks that chain together vulnerabilities.
As in:
When a hacker finds one small rupture in site security, their software will immediately check for more. A domino effect sets off, launching a multi-step cyberattack on your entire WordPress site.
2. When AI joins the forces
AI is now part of both sides of the security equation.
At Patchstack, researchers have identified AI-generated WordPress plugins that ship functional code, but with hidden vulnerabilities.
Why? Because their authors often lack real coding experience and skip proper security validation, unlike a human reviewer who understands secure coding patterns. These are the ideal places for blind spots.
AI tools can:
- Write and publish code instantly — even if it’s insecure.
- Analyze code to find exploitable mistakes like a bloodhound.
- Auto-generate scripts to weaponize vulnerabilities before patches exist.
- Create polymorphic malware — code that changes its signature to evade traditional scanners.
That’s a complete shift in how fast and how intelligently exploits spread.
For example:
In August 2025, Slider Revolution—a plugin used by 4 million sites—was found to be vulnerable. It allowed attackers with contributor-level access to read sensitive server files and exposed credentials and private data.
It’s a textbook example of what happens when a popular, trusted plugin becomes a massive attack surface overnight.
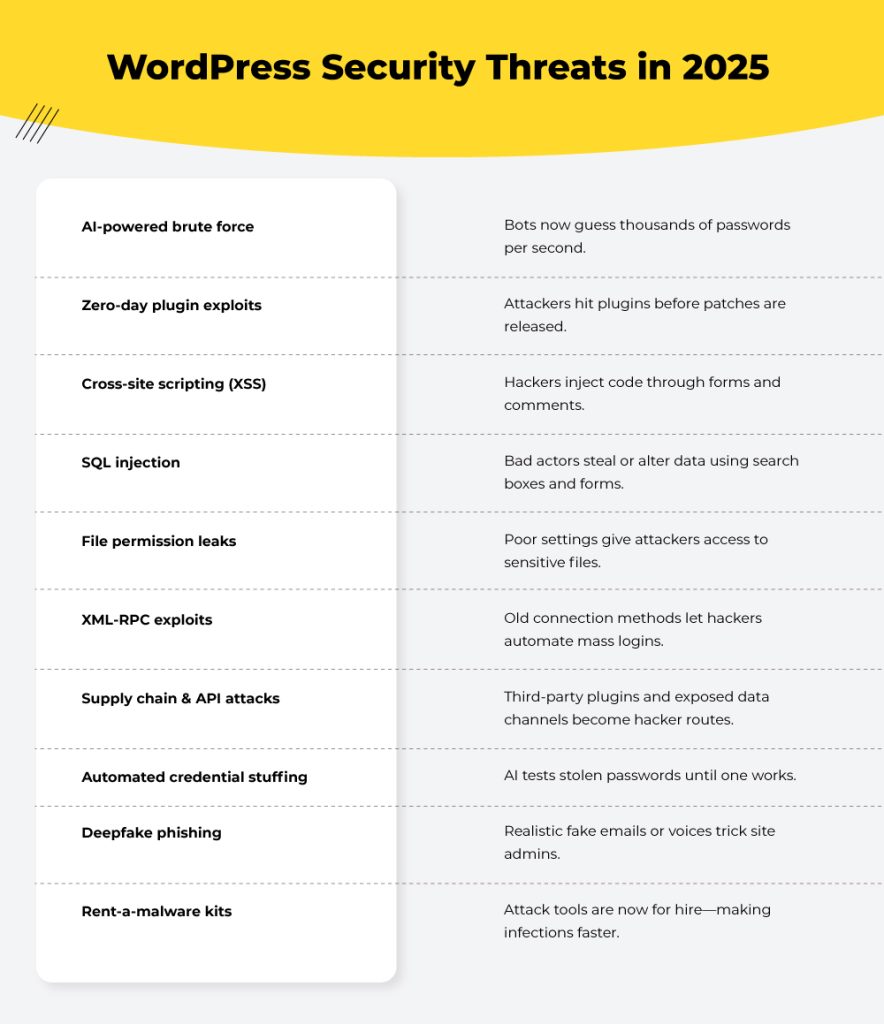
3. The most common WordPress threats in 2025
Here’s how attacks are evolving this year:
AI-fueled brute force attacks
Bots make thousands of login attempts per second. They learn from failed attempts and bypass basic WordPress login security.
Zero-Day plugin exploits
AI scanners hunt for plugins and themes with flaws that haven’t yet been patched. They do so across thousands of sites at once in real time.
Cross-site scripting (XSS)
Comment forms and unsecured inputs become the injecting valve for malicious scripts. Through which, hackers steal cookies, redirect users, or hijack admin sessions.
SQL injection
Unfiltered data entry points (such as search boxes or forms) allow attackers to extract or alter database content. AI now automates these attacks at scale.
File permission leaks
Loose file settings can let attackers modify core files or inject malicious code directly.
XML-RPC exploits
XML-RPC is an old protocol that lets external apps and tools communicate with your WordPress site. Even though it’s less used today, the xmlrpc.php file is present on almost all WordPress installs.
Leaving xmlrpc.php open makes your website an easy target for brute-force and DDoS attacks.
Supply chain & API vulnerabilities
Hackers now exploit third-party software your site depends on, not the site itself. A less secure partner is the easiest target for attackers trying to infiltrate your network.
Also, with headless WordPress separating the backend from the frontend , more API endpoints are exposed for data exchange.
If not properly secured, hackers can exploit API flaws to access your data or control your site remotely.
Even more to worry about….
- Automated stuffing of credentials. AI tools test stolen username-password combinations.
- Deepfake-based social engineering. Realistic voice or video messages tricking admins into granting access.
- AI-generated phishing pages. Fake login portals that look harmlessly perfect.
- Malware-as-a-Service. Ready-to-rent attack kits that are updated for WordPress sites.
If this caught your attention, you’ll find our related blog helpful here –Top 10 WordPress Development Trends to Follow in 2025
Advanced WordPress security best practices for 2025
1. First things first: build a strong foundation
When you’re deep in the grind, it’s easy to lose sight of the basics. Give your all to advanced WordPress security practices, but make sure the basic measures are in place first.
Here’s the checklist of must-haves to secure your WordPress website.
- Never miss updating WordPress core, themes, and plugins.
- Make unique passwords a habit. Turn on Two-Factor Authentication (2FA).
- Limit login attempts. Always change the default “admin” username.
- Set proper file permissions and disable file editing via the dashboard.
- Regular, off-site backups are your safety net; test restoring them!
- Pick a reputable host that promises built-in security features.
- Consider Cloudflare or similar services for DNS-level protection.
- Encrypt data with a valid SSL/TLS certificate and automate renewals.
- Apply the principle of least privilege for all users, and disable dashboard file editing entirely.
2. Harden the server
Most attacks bypass the dashboard and target the server first.
- For instance, your wp-config.php file. It guards your site’s crown jewels — database credentials, security keys, etc. So, lock down the wp-config.php. Use restrictive permissions 400 (read-only for owner) or 440 (read for owner and group). and store it above the public root if possible.
- Disable file edits. Disable WordPress file editing. Use the dashboard (DISALLOW_FILE_EDIT) to block attackers who get in by tampering with code.
- Turn off directory browsing in .htaccess and restrict /wp-admin access by IP or role.
- Standardize your .htaccess rules to disable directory listings (Options -Index) and restrict the wp-admin folder access by IP or role.
- Keep XML-RPC in disabled mode if not in use.
- Choose a hosting provider that treats security as infrastructure. Account isolation, DDoS mitigation, and real-time malware scanning matter more than any plugin.
- Use DNS-level filtering via Cloudflare to block malicious traffic before it reaches your server.
3. Cultivate discipline in enterprise-level access and workflow
We’ve experienced first-hand how WordPress security weakens when processes are informal.
To minimize potential misuse of WordPress at an operational level, we recommend:
- Use password managers for shared credentials.
- Log idle users out automatically.
- Track all backend activity.
- Implement version control for plugin and theme configurations to enable safe rollbacks.
4. Manage plugins
Out of all security vulnerabilities, 89% were discovered in WordPress plugins.
Primarily because they are developed by independent developers. You don’t have complete insight into their security practices.
The best safeguard against this is efficient, proactive plugin management. Consider how you can best:
- Prioritize reputable developers.
- Neutralize threats by frequent security updates.
- Lean on verified support channels.
- Avoid unmaintained or nulled plugins.
- Remove inactive and redundant plugins.
- While updating plugins, use staging environments and test updates before going live.
- Implement automated rollback procedures and audit your stack quarterly.
- Stay vigilant about supply chain attacks. Monitor security alerts for the plugins your site uses and act quickly on news of vulnerabilities.
- If you have multiple sites to manage, it’s wise to invest in centralized plugin management tools, like Solid Central.
5. Integrate continuous testing and monitoring
- Detection speed matters as much as prevention. Deploy a web application firewall (WAF) with a malware scanner. Wordfence, MalCare, and Solid Security Pro are reliable options.
- Back up your site off-site daily or in real time. Test restorations to ensure backups work.
- Configure alerts for irregular file changes, failed logins, or sudden traffic anomalies as these often signal injections, defacements, or malware deployment.
6. AI and automation can be your security team that never sleeps
- AI isn’t just for attackers. Install WordPress security plugins with real-time threat detection and automated alerts.
- Schedule regular vulnerability scans and penetration tests.
- Automate full-site backups with quick restore protocols. Trust, but verify.
7. Have a unified, auditable WordPress website security regimen
- Document and examine all security measures. From permissions and plugin policies to server configurations.
- Conduct quarterly audits covering plugin versions, SSL validity, database prefixes, and user permissions.
- Disable PHP error reporting and hide your WordPress version number. It reduces the information available to attackers.
- Maintain deployment logs. It’s great for tracking updates, rollbacks, and file changes for faster recovery and forensic analysis.
- Evaluate plugin credibility continuously. As part of this, check update frequency, developer reputation, support responsiveness, and installation metrics. These factors form a security layer beyond technical controls.
One last thing….
A multilayered and integrated approach to WordPress maintenance and security is very, very, very important.
No isolated practice keeps WordPress safe in 2025. Keeping all the shields overlapping means that if one fails, the next catches the attack. To make your digital fortress harder to crack, stitch together the following:
- Security audit.
- Automated testing.
- Development environments.
- Performance monitoring.
The road ahead
WordPress website security now means resilience. Continuous monitoring, trained teams, vetted vendors, and scalable infrastructure form the groundwork for it.
More than mitigating security threats, it’s about protecting trust, compliance, and reputation in an AI-driven web.
At Mavlers, we help brands build smarter, faster, more resilient digital foundations. With AI-powered performance optimization and custom theme and plugin development, we get your WordPress maintenance and security in line.
Ready to future-proof your WordPress site? Contact us—and let’s make your site unbreakable.


Urja Patel - Content Writer
Urja Patel is a content writer at Mavlers who's been writing content professionally for five years. She's an Aquarius with an analyzer's brain and a dreamer's heart. She has this quirky reflex for fixing formatting mid-draft. When she's not crafting content, she's trying to read a book while her son narrates his own action movie beside her.
Agentforce AI marketing: How to build full campaigns from a single prompt